Imprivata Digital Identity Solutions Overview and Architecture
The Imprivata Digital Identity Framework (DIF) provides an organized structure to help healthcare delivery organizations holistically manage, secure, and monitor their organization’s digital identities. The framework is designed around the key categories required for a robust digital identity strategy that meets the unique demands of healthcare. These categories, which align with H-ISAC’s identity framework for healthcare, include the following: governance and administration, identity management, authorization, and authentication and access.
The Imprivata DIF is represented in the diagram and includes a color-coded legend that describes how Imprivata’s digital identity solutions map to each of the capabilities defined in the framework. This guide will focus on reference architectures for implementing Imprivata Enterprise Access Management single sign-on, multifactor and advanced authentication using Imprivata Confirm ID , and mobile solutions using Imprivata Mobile Access Management (GroundControl) to support workflows with Epic EHR and Epic Rover.
The Imprivata Digital Identity Framework. Click to enlarge.
Imprivata Enterprise Access Management SSO and MFA Overview
Imprivata Enterprise Access Management for SSO is the enterprise single sign-on (SSO), authentication management (AM), virtual desktop access (VDA), and self-service password reset (SSPR) solution specifically designed for healthcare. Enterprise Access Management provides simple and secure access to both cloud and on-premises clinical and administrative applications enabling providers to instantly log into their desktop and sign into their applications with just a tap of a badge or swipe of a finger. Enterprise Access Management security also helps to protect patient data, empowering organizations to meet HIPAA compliance requirements, preventing credential-sharing, securing PHI on unattended workstations, and enabling easier and more thorough auditing and reporting of workstation and application access.
Imprivata Enterprise Access Management for MFA is a comprehensive identity and multifactor authentication solution designed for healthcare. Enterprise Access Management centralizes identity and multifactor authentication across all enterprise workflows, including remote access, cloud applications, Electronic Prescribing of Controlled Substances (EPCS), medical devices, and clinical workflows such as medical ordering, witness signing, user verification, and procedure attestation. Enterprise Access Management also supports a variety of authentication methods, including hands-free authentication, push token, fingerprint, badge, SMS, and more. Users are only prompted for those authentication methods for which they are enrolled and that are available and allowed for the specific workflow.
The sections below describe the Imprivata appliance and Imprivata agent — the key components of the Imprivata architecture — as well as design considerations for implementing SSO and MFA with the Epic EHR.
The Imprivata appliance is the foundation of the Imprivata Enterprise Access Management solutions. It is delivered as an Open Virtualization Format (OVF) image that can be hosted on the premises using VMware ESX, Microsoft Hyper-V, and Nutanix virtual environments, or within the organization’s Microsoft Azure tenant. The appliance is configured to synchronize with Microsoft Active Directory (AD) to import user identities into Imprivata Enterprise Access Management.
User identities can be imported based on either organizational units (OUs), security groups, or individual users; and enabled for single sign-on and other EAM capabilities. During a user authentication event, the Imprivata appliance performs an LDAP bind to Active Directory to verify a user’s status. A single appliance can handle thousands of simultaneous authentication events from Imprivata-enabled workstations.
The following diagram shows Imprivata appliances as they would commonly be deployed and depicts other network services and infrastructure to support the appliance’s operations, management, and interfaces to supporting systems. Some of the network services are customer systems hosted on-premises or in the customer’s cloud infrastructure. Imprivata appliances also communicate with Imprivata cloud services to integrate and support other Imprivata solutions.
Imprivata appliances and Imprivata agent high level communications architecture

The Imprivata appliance uses a SUSE Linux-based operating system and is hardened to ensure the highest level of security. Access to the Appliance is restricted to HTTPS (SSL) on port 443 for the Imprivata users and Administrators and HTTPS (SSL) on port 81 for managing the appliance device settings. Data is stored on the appliance in an encrypted database. Only signed software from Imprivata can be uploaded and installed on the appliance. The Imprivata enterprise appliance infrastructure should be deployed behind boundary firewalls alongside other core infrastructure servers and should never be installed in a DMZ.
The Imprivata agent is installed on devices where Imprivata Enterprise Access Management authentication and SSO services are required. This includes Windows-based workstations, thin/zero-client devices (embedded), virtual desktop images, and shared servers (such as Citrix and VMware Virtual Application servers). It is a lightweight client that
-
Is delivered as an MSI.
-
Enforces user authentication, authorization, and user workflow management.
-
Provides SSO for enabled applications.
Imprivata agents on Microsoft-based Windows operating systems communicate with an Imprivata appliance using Imprivata Secure Exchange (ISX) — a proprietary Imprivata protocol that uses AES 256-bit encryption, which is then encapsulated in TLS for securing user data while it is in transit. Thin and zero-client devices communicate with the Imprivata appliance using Imprivata’s ProveID Web protocol — a proprietary Imprivata protocol that encapsulates in TLS for secure communication.
Imprivata appliances and Imprivata agent secure communication

Imprivata agents have intelligence to detect a communications failure to an appliance and automatically switch to other appliances within the system. To achieve this higher availability, the Imprivata agent maintains a network topology map of all Imprivata appliances along with defined failover rules that instruct the agent where to go next if it cannot communicate with an appliance.
The Imprivata agent can be configured to support a variety of workstation configurations that are frequently used in a healthcare setting:
-
Shared workstations – Windows-based shared workstations are typically configured to automatically logon to Windows using workstation-specific credentials configured and secured within the Windows registry (e.g., <Sharedkiosk10N35user>/<Sharedkiosk10N35password>) during the boot process. The Imprivata agent then secures the workstation with a customizable lock screen.
The Imprivata shared workstation lock screen. Click to enlarge.
In this model, a full Windows logon process does not occur when a user authenticates to the workstation; rather, the user’s credentials are verified against Active Directory and then the workstation is unlocked. This allows for a fast logon process and switching between users. This is referred to as Imprivata Enterprise Access Management Fast User Switching (FUS).
-
Private workstations – With Windows-based private workstations, Enterprise Access Management integrates with the standard Windows logon process. Private workstations are typically dedicated to a single user throughout an entire shift, and when they are locked, only the currently authenticated user or an administrator can unlock the session or logout the current user.
-
Shared workstations with Multi-User Desktop – The Multi-User Desktop (MUD) feature of Windows can support multiple concurrent Windows sessions on the same workstation, and when enabled using Imprivata policy, this configuration can provide another form of a shared workstation. The number of concurrent sessions and maximum lifetime of those sessions can be limited using Imprivata policy. When the number of concurrent sessions is set to one (1), the limitation of the private workstation experience described above is removed, and any user can log out the current user when authenticating to the workstation.
Imprivata agents are also installed on virtual desktop images managed within a VDI infrastructure and on Citrix and VMware Virtual Application servers hosting virtualized applications and desktops. In these scenarios, the Imprivata agent provides single sign-on and advanced authentication functionality in the virtualized environment on behalf of the authenticated user. It can also interoperate with the Imprivata agent installed on the remote workstation to provide “tap and go” access to virtualized resources using Imprivata Virtual Desktop Access.
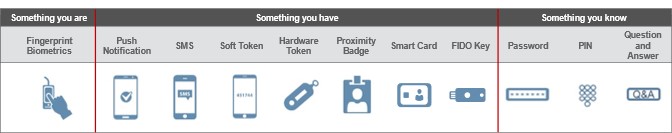
Supported Authentication Methods
The Imprivata agent supports a variety of authentication methods that can be used for primary authentication, multifactor authentication, and secondary or re-authentication with Epic Hyperdrive clinical workflows.
Supported authentication methods. Click to enlarge.
Supported authentication methods
Many of these authentication methods can be combined to support multifactor authentication (MFA) for desktop access using Imprivata Enterprise Access Management or to support various authentication workflows using MFA . For example, an Enterprise Access Management desktop authentication policy can be created to require MFA using a passive proximity card and domain password. This policy can be enabled for all authentication attempts, or it can be configured to require MFA only at the start of a shift while providing users with a grace period where they are only required to use a single factor (passive proximity card, in this example) during the remainder of their shift. Additionally, a workflow policy can be created to require MFA for Electronic Prescribing of Controlled Substances (EPCS).
Imprivata Enterprise Access Management supports a variety of desktop and application virtualization delivery solutions including Citrix DaaS and Omnissa Horizon.
In an environment that includes applications delivered via application virtualization technology, like Citrix DaaS, the Imprivata agent is installed on user workstations and on each server in the Citrix site. The Imprivata agent on the user workstation interacts with the locally installed Citrix Workspace app to authenticate to the Citrix session and launch applications and achieve single sign-on. Optionally, Citrix applications can be launched automatically using Imprivata Virtual Desktop Access. The Imprivata agent on the Citrix server provides single sign-on and advanced authentication to applications hosted in the site.
Imprivata Enterprise Access Management architecture with Citrix DaaS

In an environment that includes virtualized desktops that are delivered via Citrix DaaS or Omnissa Horizon, the Imprivata agent is installed on each user workstation and on each virtual desktop instance in the desktop pools that require application single sign-on and advanced authentication. The Imprivata agent on the user workstation interacts with the locally installed Citrix Workspace app or Omnissa Horizon Client to authenticate to and automatically launch virtualized desktops using Imprivata Virtual Desktop Access. The Imprivata agent on the virtualized desktop provides single sign-on and advanced authentication to applications installed on the virtualized desktops.
The Imprivata Enterprise Access Management architecture with Omnissa Horizon or Citrix DaaS VDI. Click to enlarge.
"Thin or zero” client workstations are an alternative to using Windows-based workstations when delivering virtualized applications and desktops. All applications are delivered to the user via application and/or desktop virtualization technologies.
These devices:
-
Can be used to deliver the same – or very similar – end user computing experience.
-
Use a lightweight operating system, which is typically Linux-based.
The authentication functionality of the Imprivata agent is built into the operating system (firmware) of most of these devices. They connect to the Imprivata Enterprise using a secure, RESTful API to retrieve configuration information and to handle user authentication requests.
-
Are generally less expensive to own and operate than Windows-based workstations.
Imprivata Enterprise Access Management supports a growing list of thin and zero client devices from vendors such as HP, IGEL, and Dell ThinOS. For a full list of supported application and desktop virtualization technologies, and thin and zero client devices, see the Imprivata Enterprise Access Management Supported Components Guide.
For more than a decade, Imprivata has worked with Epic Systems to develop the Imprivata Connector for Epic Hyperspace and now Hyperdrive. The Connector leverages Epic's authentication API to provide single sign-on, single sign-off, and fast user switching for Epic Hyperdrive.
Imprivata Enterprise Access Management offers two different configuration options for Epic that can be enabled on a per-workstation basis:
-
SSO for Multiple Applications including Epic – With this workflow, the Windows desktop is secured by the Imprivata agent between user sessions. Users authenticate to EAM using any of the Imprivata supported authentication methods — typically fingerprint or proximity card. This workflow is optimized for workstations on which EAM SSO is required for multiple applications, including Epic.
-
SSO for Epic Only workflow – With this workflow, the Windows desktop is always unlocked. Users authenticate to Epic using most of the Imprivata Enterprise Access Management supported authentication methods — typically fingerprint or proximity card. This workflow is optimized for workstations on which Epic is the most frequently accessed and typically the only application. Single sign-on /sign-off for applications other than Epic is not supported. Standard desktop security mechanisms can be used to make the desktop more secure to protect against accidental PHI exposure from other non-Epic applications. This configuration should be configured to not allow other applications to be launched as the desktop is not locked between user sessions.
Imprivata Enterprise Access Management can be configured to secure Epic and maintain the current patient context or log the user out of Epic with either of these workflows. Secure is typically used in clinical settings where a patient is provided care by multiple care providers and maintaining patient context between user sessions provides for smoother workflows. This is often seen in ambulatory settings such as exam rooms. Logout is used in other areas where maintaining the patient in context is not advantageous.
Imprivata Enterprise Access Management for Electronic Prescribing of Controlled Substances (EPCS) is an end-to-end solution for meeting the DEA requirements for EPCS, including provider identity proofing, supervised enrollment of credentials, two-factor authentication, and auditing and reporting. The Imprivata Confirm ID for EPCS license also includes the Imprivata Enterprise Access Management for Clinical Workflows license.
Imprivata Enterprise Access Management for Clinical Workflows offers advanced multifactor authentication support for more than sixty signing workflows in Epic. A few of the more common workflows enabled with Imprivata Enterprise Access Management include:
-
Anesthesia attestation – Anesthesiologists tap their proximity badge when attestation signing instead of entering their password. This saves time and improves efficiency as anesthesiologists move from room to room.
-
Medication administration record (MAR) – Some patient care procedures require a re-verification that the user logged into Epic is the one who is administering a medical. Some facilities and even states within the United States require that a user re-authenticate to ensure it is them that recorded that a medication was administered. The user taps a badge or swipes a finger to re-authenticate versus enter username and password or answering security questions.
-
Dual MAR/Med wasting/Witnessing – In patient care, frequent situations occur where a care provider must ensure there is a witness to a specific procedure. These are common to the administration of high-risk medications and blood transfusions and for wasting of controlled medications. In these situations, authorized care providers quickly and efficiently authenticate to witness that the correct medication and dosage or the correct blood type was administered, or that residual medication that was not administered to the patient was safely and properly destroyed. Instead of manually entering their username and password or answering security questions, authorized witness care providers tap a badge or swipe a fingerprint.
-
Break-the-glass – In code situations or other emergencies, Imprivata Enterprise Access Management for Clinical Workflows gives providers a fast, efficient authentication option when they need to override their assigned privileges to access patient records, order emergency medications, or complete different transactions. Instead of having to remember and manually enter a password while under duress, providers simply tap a badge to break the glass.
-
Specialty narrator – During critical events, including Trauma, Code, and Sedation, Epic Specialty Narrator is used to capture the attendance of clinical staff responding to the event. With Imprivata Enterprise Access Management, staff tap a badge to record their arrival and departure in the narrator as they enter and exit the event. There are two common ways to configure the Specialty Narrator: Integrated and Standalone.
-
Integrated specialty narrator – Using the Staff toolbox group in Epic specialty Narrators, staff can use a badge scanner to mark themselves as arrived or departed during a specialty event. Using Integrated Badge Scanning allows clinical staff to mark themselves as arrived or departed with just a scan of their badge so they do not have to interrupt documenting important patient care assessments and medications. This workflow is performed on the same workstation that clinicians are already utilizing to document patient care.
-
Standalone specialty narrator – With standalone narrator, a dedicated workstation can be configured for staff to scan in on a pre-login screen of Epic. Staff can approach the workstation and tap their badge to mark themselves as arrived or departed. This dedicated workstation can act as a hub for a group of care rooms in a department. A standalone badge scanning workstation might be more suitable for trauma events, while integrated badge scanning might be more suitable for code or sedation events where having a separate workstation isn't always feasible.
-
Imprivata has worked with Epic Systems to develop the Imprivata Connector for Epic so that it integrates with Hyperdrive when accessed via Epic Community Connect (where Hyperdrive is hosted by another health organization). The Connector leverages Epic’s Slingshot authentication API to provide single sign-on, single sign-off, fast user switching, and advanced multifactor authentication workflows for Epic Hyperdrive.
Imprivata Enterprise Access Management currently offers SSO for the Multiple Application configuration option for Epic Community Connect, which can be enabled on a per-workstation basis:
-
SSO for multiple applications including Epic – With this workflow, the Windows desktop is secured by the Imprivata agent. Users authenticate to Enterprise Access Management using any of the supported authentication methods — typically fingerprint or proximity card. This workflow is optimized for workstations on which Imprivata SSO is required for multiple applications, including Epic.
Enterprise Access Management can be configured to secure Epic and maintain the patient context or log the user out of Epic with this workflow.
Enterprise Access Management for Electronic Prescribing of Controlled Substances (EPCS) is an end-to-end solution for meeting the DEA requirements for EPCS, including provider identity proofing, supervised enrollment of credentials, two-factor authentication, and auditing and reporting. The Enterprise Access Management for EPCS license also includes the Imprivata Confirm ID for Clinical Workflows license.
Enterprise Access Management for Clinical Workflows offers advanced multifactor authentication support for more than sixty signing workflows in Epic, including, but not limited to:
-
Anesthesia attestation – Anesthesiologists can tap their proximity badge when attestation signing instead of entering their password. This saves time and improves efficiency as anesthesiologists move from room to room.
-
Medication administration record (MAR) – Some patient care procedures require a re-verification that the user logged into Epic is the one who is administering a medical. Some facilities and even states within the United States require that a user re-authenticate to ensure it is them that recorded that a medication was administered. The user taps a badge or swipes a finger to re-authenticate versus enter username and password or answering security questions.
-
Dual MAR/Med wasting/Witnessing – In patient care, frequent situations occur where a care provider must ensure there is a witness to a specific procedure. These are common to the administration of high-risk medications and blood transfusions, and for wasting of controlled medications. In these situations, authorized care providers can quickly and efficiently authenticate to witness that the correct medication and dosage or the correct blood type was administered, or that residual medication that was not administered to the patient was safely and properly destroyed. Instead of manually entering their username and password or answering security questions, authorized witness care providers taps a badge or swipes a fingerprint.
-
Break-the-glass – In code situations or other emergencies, Enterprise Access Management for Clinical Workflows gives providers a fast, efficient authentication option when they need to override their assigned privileges to access patient records, order emergency medications, or complete different transactions. Instead of having to remember and manually enter a password while under duress, providers can simply tap a badge to break the glass.
-
Specialty Narrator and Willow Ambulatory are currently not supported with Enterprise Access Management with Epic Community Connect.
If the instance of Epic that the Community Connect host is providing to their Community Connect sites is hosted on the same Citrix/VMware server image that the host uses internally, there are additional steps required by both the host and site to configure Enterprise Access Management for EPCS and Clinical Workflows. Contact your Imprivata Enterprise Managed Services or Professional Services team for configuration details.
Imprivata Enterprise Design
An Imprivata enterprise consists of at least two Imprivata appliances that service authentication requests from a collection of Imprivata agents. The appliances are configured to connect to existing IT infrastructure including:
-
AD domain controllers
-
DNS servers, NTP servers, SMTP servers for alerts
-
FTP servers or file shares for storing backups, offloading archived audit data, and storing reports
The connections between the Imprivata agents and the Imprivata appliances use the secure ISX protocol.
Imprivata recommends deploying at minimum a single appliance in each of two data centers to provide data center-level redundancy. In this configuration, the data stored within each appliance in the two data centers is replicated to the peer appliance in the alternate data center. Imprivata agent connect to the appropriate appliance based on site configuration and appliance availability.
Two or more appliances are configured to create an Imprivata enterprise. Appliances are designated as either a database appliance or a service appliance.
Database Appliances
Database appliances host replicas of all enterprise data comprising a collection of user and computer policies, application profiles, user and computer objects, and the defined interrelationship between each of these elements. Changes to any data item is replicated in real time to the peer database appliance.
There are a maximum of two database appliances typically deployed to separate data centers that can be configured as active-active or active-passive for high availability purposes. An Imprivata enterprise should always have two database appliances to ensure database and audit continuity if one database appliance becomes unavailable. Data replication consumes network bandwidth, so one database appliance per site is enough for most enterprise needs. Database replication occurs only between the database appliances, not to service appliances.
A minimum configuration of an Imprivata enterprise would be two (2) database appliances that should ideally reside in different datacenters. The first two appliances created for an enterprise are database appliances. Thereafter, any additional appliances created are service appliances. For a multisite enterprise as shown below, the first site will be created as the enterprise is created. The second site should be created as the second database appliance is added. If not, the second database appliance will be added to the first site. As the first two appliances created within an enterprise are always database appliances, they should be added to the appropriate desired site before any service appliances are added.
Imprivata enterprise fault-tolerant architecture

Service Appliances
Service appliances are added to increase capacity by sharing authentication events and offloading that workload from the database appliance. These appliances differ from database appliances in that they do not host replicated database tables containing Imprivata configuration, user information, and audit data. A service appliance should reside in the same data center as its corresponding database appliance to reduce the time needed for the service appliances to service requests from endpoint Imprivata agents.
After the first two (2) appliances (database appliances) are added, any additional appliances created will be service appliances. For a multisite enterprise as shown above, both sites should be created as the first and second database appliance is added. This must be completed before a service appliance is added to a site. A new service appliance can then be added to either site. Typically, sites have an equivalent number of database and service appliances.
Imprivata conducted exhaustive performance testing to allow individual appliances to increase throughput by increasing CPU resources. In general, up to four (4) appliances within the enterprise could scale linearly by adding more vCPU resources to each appliance. This meant that an appliance could double the throughput of its primary job of authenticating sessions simply by increasing the vCPUs for the appliance virtual machine from two (2) vCPUs to four (4) vCPUs. With four (4) or fewer appliances within the enterprise, this linear scaling was found to be very accurate. In fact, each appliance could attain a four-fold increase in throughput over the default two (2) vCPUs by increasing the vCPUs to a total of eight (8) for each appliance. This provided additional options for organizations that needed to increase enterprise capacity but did not want to add additional appliances.
Imprivata Enterprise Active-Active Architecture with Service Appliances. Click thumbnail to enlarge.
Using the new testing parameters, Imprivata developed new standards for enterprise sizing and scaling. With the new architecture, two appliances will host and support the full database. For fourth generation 4 (G4) and later Imprivata enterprises, Imprivata recommends three standard architecture options: two-, four-, and six-appliance enterprises. The two-appliance enterprise offers three different CPU and RAM configuration options for scale.
Two-appliance Imprivata enterprise

Sites with the database appliances and service appliances should typically be balanced such that there is an equal number of service appliances for each database appliance.
Four-appliance Imprivata enterprise

Six-appliance Imprivata enterprise

At this time, Imprivata does not provide recommendations beyond the six-appliance enterprise. Load testing does not indicate that an appreciable increase in concurrent user-session capacity is achieved by adding more than two service appliances to each site or database appliance.
| Recommended Options | 2 Appliance Enterprise | 4 Appliance Enterprise | 6 Appliance Enterprise | ||
|---|---|---|---|---|---|
| Database appliances | 2 | 2 | 2 | 2 | 2 |
| CPUs per appliance | 4 | 8 | 8 | 8 | 8 |
| RAM (GB) per appliance | 8 | 16 | 32 | 16 | 16 |
| Service appliances | 2 | 4 | |||
| CPUs per appliance | 2 | 2 | |||
| RAM (GB) per appliance | 8 | 8 | |||
| Total appliance CPUs in enterprise | 8 | 16 | 16 | 20 | 24 |
| Total appliance RAM in enterprise | 16 | 32 | 64 | 48 | 64 |
| Number of user sessions supported (in optimal conditions) | 22,000 to 28,000 | 28,000 to 36,500 | 36,500 to 47,500 | 47,500 to 62,000 | 62,000 to 80,000+ |
Imprivata Mobile Access Management Overview
Imprivata Mobile Access Management (formerly GroundControl) delivers automated setup and check-in / check-out workflows for shared mobile devices. The solution helps optimize the workflows for users of mobile devices while improving security and auditability. When used in conjunction with Imprivata Enterprise Access Management, MAM provides proximity card-based device check out and credential autofill for mobile applications, which further streamlines mobile workflows.
The sections below describe the key components of Imprivata Mobile Access Management including the cloud tenant and associated management console, the Launchpad, smart hubs, mobile devices, mobile device management (MDM), and the Locker mobile application. Design considerations for implementing MAM with Epic Rover are also provided.
Imprivata Mobile Access Management logical architecture. Click thumbnail to enlarge.
Imprivata Mobile Access Management is a hybrid solution that consists of on premises and cloud components. Administrators can manage the solution using a cloud-delivered, web-based management console. The console allows MAM administrators to configure mobile device workflows and automations and manage Launchpads and devices.
Most customers are deployed on MAM’s multi-tenant cloud; however, some prefer a dedicated cloud environment. A dedicated cloud is physically isolated from other customers and is still managed by Imprivata, however, it allows an organization to receive GroundControl software updates on a delayed and controlled release cadence. Dedicated clouds have the same high-availability infrastructure as the shared cloud environment.
The Imprivata Mobile Access Management Launchpad software is installed on dedicated Apple Mac or Microsoft Windows workstations that are co-located with mobile device smart hubs. The Launchpads receive instructions from the Imprivata Mobile Access Management cloud environment and interact with attached smart hubs and connected mobile devices to support various shared device workflows.
When the Launchpad software is used with Windows-based hardware, it is highly recommended that the hardware be thoroughly tested with large quantities of connected mobile devices (20+). Windows-based hardware capabilities vary between different manufacturers, and testing is required to ensure reliability and scalability of the Imprivata Mobile Access Management solution.
-
The Launchpad workstations must be configured for unattended use, and since the software runs as a foreground service, the workstations must automatically log in as a user that should not have administrator privileges.
-
Headless workstations without displays are preferred, and the workstations must be configured to automatically restart in case of unexpected shutdowns.
-
Protected power outlets are recommended whenever possible.
-
The workstations should also have reliable connectivity to the Imprivata Mobile Access Management cloud environment; therefore, a hardwired network connection is required.
-
When using the check-in / check-out capabilities of Imprivata Mobile Access Management with Imprivata Enterprise Access Management, a USB-connected proximity card reader is required, however, the Imprivata agent is not required and should not be installed on these workstations.
-
Workstation management policies and security software that limit USB functionality may need to be removed or altered to allow the use of smart hubs and proximity card readers.
Smart hubs are used to store, recharge and sometimes secure shared mobile devices. They are connected via USB to workstations that have the Imprivata Mobile Access Management Launchpad software installed. The Launchpad software is used to configure the devices that are connected to the smart hubs during device setup and check-in / check-out workflows.
Smart hubs come in a variety of different models and sizes and can accommodate shared mobile phones as well as shared tablets. They are offered in two form factors including device trays and docks. Imprivata Mobile Access Management only supports smart hubs that are qualified and sold by Imprivata.
Imprivata Mobile Access Management Smart Hub Options

Smart hubs charge mobile devices to their maximum power faster than ordinary hubs. They support a variety of different cabling options including USB-C and Apple Lightning. Imprivata Mobile Access Management uses special integrations with the smart hubs to report the port number of each connected device and communicate status to users via integrated LEDs. Up to two smart hubs may be connected to a single Mac or Windows workstation when used with the Launchpad software.
The Imprivata Mobile Access Management solution supports managing a fleet of shared mobile devices. Apple devices enrolled in the Apple Device Enrollment Program (DEP) are supported as well as non-DEP devices. Devices must be managed by a Mobile Device Management (MDM) solution (see section on mobile device management) and used with smart hubs connected to workstations running the Launchpad software.
When using protective cases on shared mobile devices, their size must be considered when selecting smart hubs as they may require different smart hub slot sizes versus using the devices without cases. Cases with batteries are not supported, as the batteries interfere with power and data. The mobile devices should also have reliable Wi-Fi network connectivity to the Imprivata Mobile Access Management cloud environment and to the Imprivata enterprise.
Imprivata Mobile Access Management requires devices that are managed using a supported Mobile Device Management (MDM) solution. Imprivata Mobile Access Management does not replace the functionality of an MDM, rather, it works alongside industry leading MDMs to trigger actions that are typically performed manually such as clearing device passcodes using API-based integrations.
There are several required items that must be configured in the MDM to support Imprivata Mobile Access Management. For more information, see the Imprivata Mobile Access Management Implementation Guide.
The Imprivata Locker application is used to manage mobile device authentication (sign in and out) and credential autofill when used in conjunction with Imprivata Enterprise Access Management.
Credential autofill is not fully equivalent to single sign-on/sign-off (SSO). Users still need to sign into multiple apps, but the sign in process is dramatically easier. Autofill by itself does not alter the application logout process.
Imprivata distributes the Locker app through Apple’s Custom App feature within Apple Business Manager. The application requires support for notifications that can be configured via the MDM. The Locker application supports using a PIN or the user’s domain password as a second factor for credential autofill.
Imprivata locker application: locked device (left) and unlocked device (right)
For more information, see the Imprivata Mobile Access Management Implementation Guide.
Imprivata Mobile Access Management fully supports shared mobile workflows with Epic’s Rover application on iOS devices. When used in conjunction with Imprivata Enterprise Access Management, proximity card-based device check out and credential autofill is also supported.
The following design considerations are recommended when implementing MAM to support workflows with Epic Rover:
-
Smart hubs – Users are required to retrieve shared mobile devices at the beginning of their shift (or when needed during their shift) using the MAM check out process from smart hubs connected to Launchpad-enabled workstations. The Launchpad-enabled workstations and the attached smart hubs should be installed in locations that are easily accessible by clinical users but not in patient pathways. Physical space requirements for the smart hubs and the associated Launchpad-enabled workstation should also be considered in locations where they are needed. The number of mobile devices required for a shift in a given department will dictate the size and number of smart hubs that are required. Sizing should also consider mobile devices being returned at the end of a shift with depleted batteries and the need for fully charged devices for users associated with the next shift.
-
Check out process – It is highly recommended to use Imprivata Enterprise Access Management in conjunction with Imprivata Mobile Access Management to support device check out workflows using proximity cards. With EAM integration, users simply tap their proximity cards on the readers attached to MAM smart hubs and Launchpad-enabled workstations to initiate the device check out process. The process is similar to authenticating to Imprivata OneSign-enabled workstations using proximity cards. If users have already enrolled their proximity cards with EAM, the badges will work with MAM without further enrollment. Since the smart hubs and associated Launchpad-enabled workstations typically do not include monitors, audible and LED cues are provided to users to indicate check out status. Users should be informed of these cues during the training process for MAM.
It is also recommended to configure MAM to display the user’s name on the Locker application when checking out a device so the user associated with the device is easily identifiable. For more information on implementing device check out, see the Imprivata Mobile Access Management documentation.
-
Mobile applications – Applications including Epic Rover and clinical communications tools are installed on the mobile devices using the MDM solution. The list of applications required by each department or clinical function may vary, and most will require some form of authentication. When used in conjunction with EAM, application profiles are created and deployed from EAM to provide credential autofill for mobile applications. For more information, see the Imprivata Mobile Access Management documentation.
As previously mentioned, users may need to log out of autofill-enabled applications manually before returning a device to a smart hub. The list of applications that have been validated for autofill and auto-logout are listed on the application support portal for Imprivata Mobile Access Management.
-
Network – Launchpad-enabled workstations and shared mobile devices must be able to reliably communicate with the Imprivata Mobile Access Management cloud and with the Imprivata enterprise. A hardwired network connection is required for all Launchpad-enabled workstations, and robust and reliable wireless coverage is recommended for the mobile devices in all locations where they will be used.
-
Check-in process – Before returning a device to a smart hub, users will need to manually log out of most mobile applications. Applications that support auto-logout are listed on the application support portal for MAM. To check in a device, a user simply returns and re-connects it to a smart hub. The user should wait to confirm the associated smart hub LED illuminates before walking away. The application logout and check-in processes should be reviewed during end-user training.
-
Overdue devices – Checked out devices that aren’t returned after a specified number of hours can become overdue, and individuals such as IT administrators can be notified accordingly via e-mail. If desired, MAM can trigger Apple’s “Lost Mode” (if using a supported MDM) to lock down the device over the air. MAM automatically removes lost mode when the device is returned to any smart hub connected to a Launchpad-enabled workstation.